The IBM Cost of a Data Breach 2024 report revealed that the average breach cost in the financial sector soared to $6.08M. That is 22% above the median across industries. With its wealth of sensitive data and direct access to monetary assets, the banking, financial services, and insurance (BFSI) industry remains a prime target for cybercriminals. This highlights the vital role of cybersecurity in banking to mitigate risks and safeguard operations.
So, what are the most pressing threats the BFSI sector faces, and how can organizations protect themselves? We gathered insights from our security specialists to explore the main threats and practical strategies to help you strengthen defenses.
Common security threats in banking
Banking institutions face multiple cyber threats daily. Here are the most prevalent threats confronting cybersecurity in the banking sector today:
- Social engineering attacks: Among the most common threats, cybercriminals employ deceptive tactics such as fake emails, calls, or messages mimicking banks to steal credentials or lure users into malicious actions. These include phishing and business email compromise (BEC), exploiting human error more than technology.
- Malware and ransomware attacks: Malware infiltrates systems, stealing data and disrupting operations. Ransomware encrypts data, demanding payment for access, often targeting banks due to their high-value data and funds. These threats affect financial systems, like ATMs and POS, and necessitate strong endpoint security.
- Distributed Denial of Service (DDoS) attacks: Overwhelming bank systems with traffic, DDoS disrupts online services like websites or apps. They cause financial losses and erode trust, often masking other crimes such as data theft.
- Insider threats: Whether intentional or accidental, these threats emerge from employees or contractors misusing access to leak data or expose vulnerabilities. Difficult to detect, they demand strict access controls and continuous monitoring.
- Advanced Persistent Threats (APTs): Sophisticated and long-term, APTs are executed by well-funded groups that stealthily target banks for data theft or disruption. Impacting critical systems like SWIFT poses systemic risks.
- Third-party and supply chain attacks: Reliance on third-party vendors for services like payment processing introduces vulnerabilities. A breach at a vendor can compromise banks through software or APIs.
- Unencrypted data: In transit or at rest, data is vulnerable to interception, risking identity theft or fraud. Despite regulations like GDPR, lapses still occur.
- Application programming interface (APIs) vulnerabilities: Widely used for integrating services and fintech partnerships, APIs can expose sensitive data or allow unauthorized access if poorly secured due to misconfigurations or inadequate authentication.
- Mobile banking malware: Targeting smartphones, malicious software intercepts SMS-based two-factor authentication codes, logs keystrokes, or overlays fake login screens to steal credentials. Often spread via unofficial app stores or phishing links, these threats compromise customer security.
Top 8 essential solutions for banking cybersecurity
Cybersecurity in banking relies on key technologies and approaches that establish robust security foundations. We gathered the main solutions used by specialists in the BFSI sector to detect threats, safeguard sensitive data, and ensure operational resilience.
Data encryption
Encryption is a cornerstone of banking security, transforming sensitive customer data into unreadable code accessible only to authorized parties. It protects personal information and online transactions, whether the data is at rest, in transit, or in use. By implementing robust encryption protocols, banks can comply with regulatory frameworks like PCI DSS or GDPR, providing end-to-end security for customer data and mitigating risks of unauthorized access.
Multi-factor authentication (MFA)
MFA adds critical layers of security by requiring multiple forms of verification, such as passwords, SMS codes, or app-based tokens, before granting access to banking systems or accounts. Additionally, adaptive MFA, which evaluates contextual factors like location, device, and user behavior, can further enhance security by adjusting verification requirements based on perceived risk levels. Our security experts recommend integrating MFA across customer-facing platforms and internal systems to safeguard against phishing and credential theft.
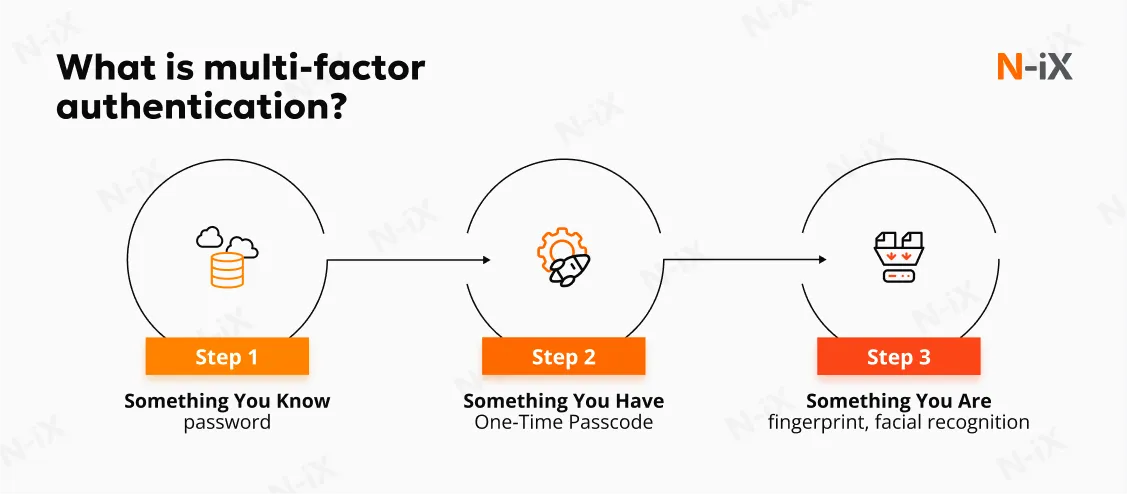
AI-driven threat detection and response
Financial institutions leverage AI to bolster defenses and protect assets. AI-powered tools analyze vast data volumes in real time, detecting patterns and anomalies often missed by human analysts. These tools enable scalable threat detection through continuous monitoring, security log analysis, and automated incident responses. Banks adopting AI and ML for fraud detection have seen significant improvements due to faster detection times, reduced false positives, and more accurate identification of suspicious activity.
Zero Trust principle
Zero Trust architecture is based on the "never trust, always verify" principle, requiring authentication for every user, device, and transaction, regardless of location. By employing micro-segmentation to isolate network segments, Zero Trust limits attackers' ability to move laterally after a breach. This approach significantly enhances visibility into traffic and activities, helping banks reduce breach detection times.
Security Information and Event Management (SIEM)
SIEM systems are indispensable for protecting financial data and ensuring regulatory adherence. These solutions aggregate and analyze data from diverse sources, detecting suspicious activities and providing real-time alerts. SIEM enables continuous transaction monitoring and rapid incident response, helping prevent significant losses from complex attacks.
Network security surveillance
Network-level visibility is vital for protecting high-value payment systems and maintaining robust cybersecurity in the banking industry. Tools that monitor traffic at the packet level detect anomalies before threats escalate. They categorize traffic from thousands of applications, enabling immediate identification of suspicious transfers. Integrating these tools with SIEM provides a comprehensive threat analysis, enhancing and speeding up security operations center (SOC) responses.
Application security solutions
Continuous monitoring of application layers detects behavioral anomalies and prevents attacks. N-iX security experts confirm that banks need secure software delivery methods to minimize data breach risks and regulatory penalties. Application security validation employs static, dynamic, and interactive testing to identify vulnerabilities. Complementing this process, automated responses, secure code reviews, and vulnerability prioritization ensure timely and effective remediation.
Biometric authentication with IAM
Identity and access management solutions (IAM) ensure that only authorized individuals access specific systems and data within a bank's ecosystem, using role-based access controls, single sign-on (SSO), and regular audits of user privileges to minimize insider threats and unauthorized access. Complementing IAM, biometric authentication utilizes unique identifiers, such as iris scans, fingerprints, voice, or facial recognition, to verify user identities. Our experts emphasize the combined importance of managing complex user bases while enhancing security through seamless yet robust authentication in mobile apps and internal systems.
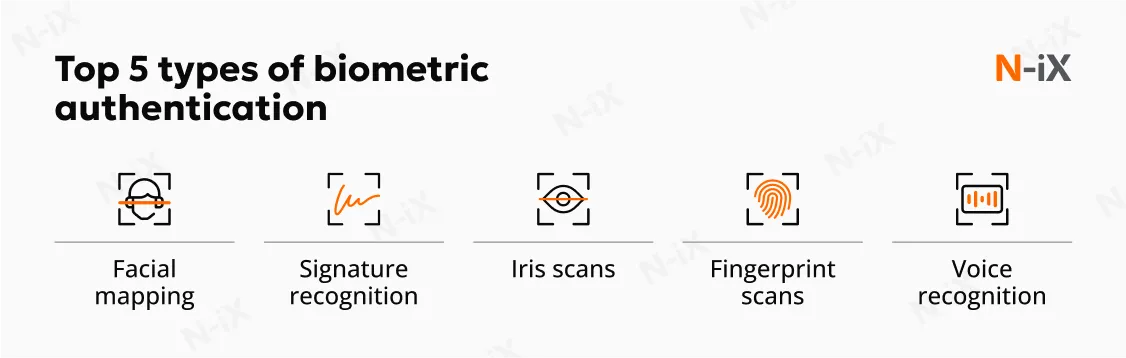
Key best practices for strengthening cybersecurity in banking
Protection technologies provide defense layers, but consistent practices determine security success. We gathered the main effective strategies according to our security experts to help banking organizations enhance comprehensive protection:
Conduct regular security audits
N-iX security specialists strongly recommend conducting regular security audits to identify vulnerabilities and gaps in banking systems before they can be exploited. These audits should cover network infrastructure, applications, and compliance with regulations like PCI DSS and GDPR. Risk assessments should focus on evaluating operational resilience, cybersecurity practices, and the management of external dependencies. By regularly assessing security controls and configurations, financial institutions can address weaknesses proactively, ensuring robust defenses against potential breaches.
Keep software updated
Cybercriminals often exploit outdated software as a primary entry point. Our experts advise BFSI companies to maintain a strict schedule for updating all software, including operating systems, applications, and security tools. Timely patches and updates close known vulnerabilities, reducing the risk of exploitation. Implementing automated patch management systems can streamline this process, ensuring no critical updates are missed.
Implement strong password policies
Weak passwords remain a significant security risk. N-iX security specialists recommend enforcing strong password policies across all banking systems, requiring complex combinations of characters, regular password changes, and the prohibition of reuse. Coupling this with multi-factor authentication provides an additional security layer, complicating attackers' access even if passwords are compromised.
Employ strong access сontrols with PAM
Careful management of access to sensitive data and systems is critical for minimizing insider threats and external breaches. Our team suggests implementing access controls guided by the PoLP (principle of least privilege), restricting user access to only the resources required for their specific roles. Additionally, privileged account management (PAM) should be prioritized to monitor and secure accounts with elevated access, using tools to track activities and detect anomalies in real time. In a sector where data confidentiality and regulatory compliance are essential, robust access management strategies are fundamental to strong cybersecurity in finance.
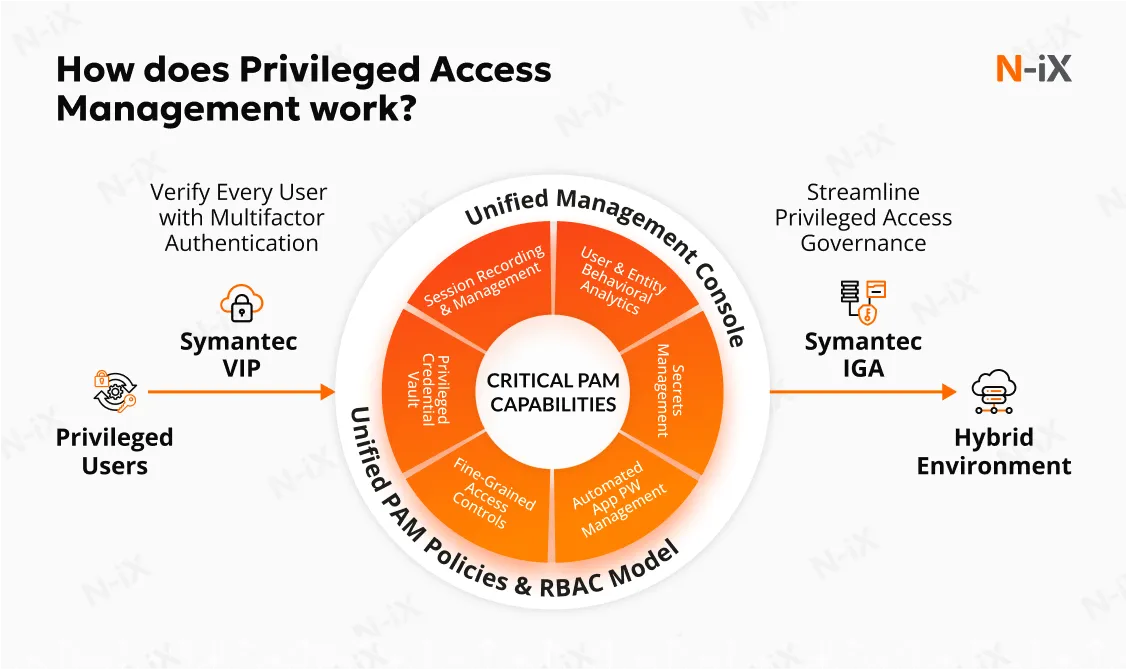
Develop incident response plans
Preparation is a key to minimizing damage from cyber incidents. Banks should develop comprehensive incident response plans that outline clear steps for detection, containment, eradication, and recovery. These plans should include predefined roles, clear responsibilities, communication protocols, notification procedures, documentation requirements, and regular testing to ensure readiness. A well-executed response can significantly reduce financial and reputational losses during a breach. We also recommend conducting retrospective meetings to learn from incidents and improve processes without assigning blame.
Force the culture of continuous improvement
Cybersecurity is an ongoing process, not a one-time task. It is crucial to force a culture of continuous improvement, where banks regularly evaluate and refine their security strategies based on emerging threats, new technologies, and lessons learned from past incidents. Focus on measuring baseline performance metrics and identifying improvement areas. Feedback and open communication provide visibility and enable collaboration for greater efficiency and transparency. Leveraging threat intelligence and benchmarking against industry standards also helps banks adapt to the evolving landscape.
Conduct regular employee training
Despite technological advancements, human error remains a leading threat to cybersecurity in banking. Our N-iX team recommends conducting regular training to help employees recognize phishing attempts, adhere to security protocols, and report suspicious behavior. Simulated attack exercises, such as phishing drills, can reinforce learning while fostering a security-conscious culture that ensures employees remain vigilant against threats.
Conclusion
The banking sector faces an ever-evolving array of cybersecurity threats, from social engineering and malware to APTs and IoT vulnerabilities, each posing significant risks to data integrity and customer trust. To mitigate these threats, banks must leverage key applications such as AI-driven threat detection, Zero Trust architecture, or biometric authentication, creating a multi-layered defense strategy. Complementing these technologies, best practices like regular security audits, strong password policies, incident response planning, and continuous employee training are essential for building robust cybersecurity in banking. Looking ahead, future trends, like the use of GenAI or blockchain for secure transactions, will redefine the cybersecurity landscape, demanding proactive adaptation from financial institutions.
As these challenges and opportunities converge, partnering with a trusted security consultant can make all the difference. N-iX is a reliable vendor for companies seeking expert guidance in cybersecurity, offering tailored solutions and deep industry insights to safeguard banking operations. With certifications in ISO 27001, ISO/IEC 27701:2019, SOC, GDPR, and PCI DSS, N-iX is equipped to secure services, from assessment and implementation to ongoing support. We successfully delivered over 250 finance projects to companies of various sizes, helping them renovate their operations while protecting their assets. Ready to fortify your defenses? Contact N-iX today to explore how we can help secure your financial future.
Have a question?
Speak to an expert




