In 2017, a large American credit score agency Equifax was hit by a massive cyber attack. It cost the company over $700M in penalties and remediation efforts. Not only did the breach succeed, but it also lasted undetected for 76 days, allowing attackers to steal the personal data of 147 million people. Sounds harsh, right?
Good news is that cybersecurity practices have evolved significantly since then. Today, with the help of AI threat detection, an attack like this could be prevented or identified within minutes rather than months. Due to AI, companies are able to counter increasingly sophisticated attacks and identify threats faster.
In a world where malicious actors weaponize AI to launch overwhelming attacks, it’s critical to employ it for defense as well. How to do that? Learn in our expert guide.

Traditional threat detection vs AI: What’s the difference?
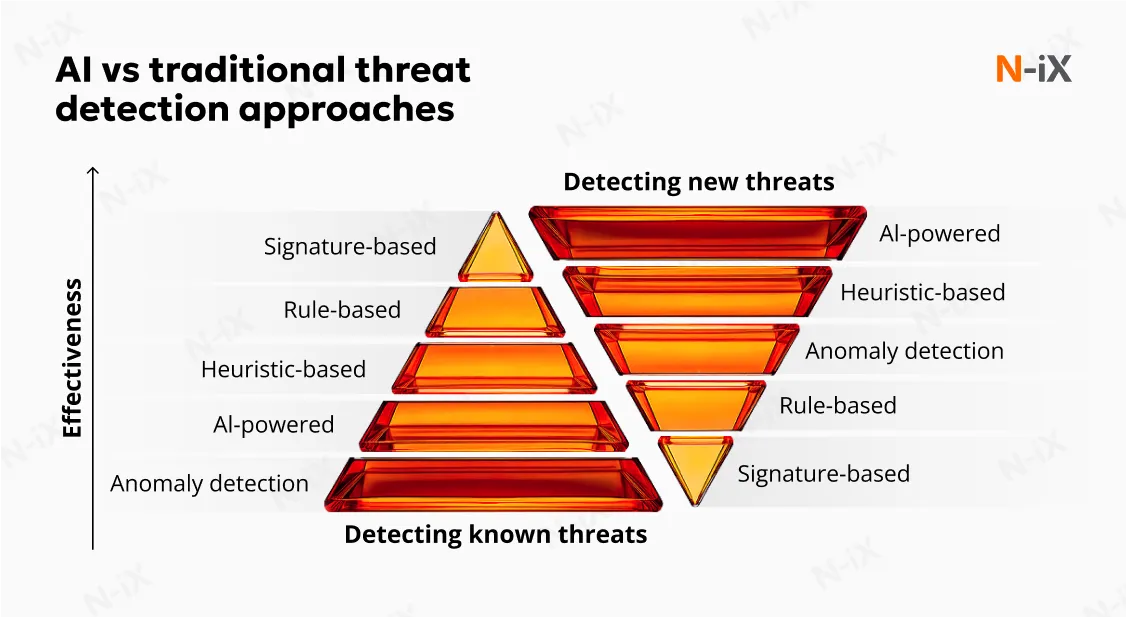
AI isn’t a one-size-fits-all solution to cybersecurity challenges. Instead, it’s a powerful tool that can supplement and sometimes replace more limited methods. To see how AI fits in, let’s take a look at several widely used traditional approaches to threat detection and where they fall short.
- Signature-based detection relies on known digital fingerprints of malware, attack patterns, or code snippets. Once researchers identify a new threat, a signature is created and pushed to all systems using that signature database. The main limitation of this approach is that it only detects what’s already known, making it ineffective against zero-day attacks.
- Rule-based security systems work by analyzing events against a set of predefined rules. Unlike signature-based approaches, they search for specific patterns rather than known threats. For instance, you can add a rule that defines a user logging in from two countries within 10 minutes as suspicious behavior. Such systems can sometimes catch unknown threats, but they are limited to their rulebook.
- Heuristic-based threat detection is a combined approach that uses both expert rules and algorithmic logic, such as scoring systems or decision trees. It offers more adaptability than other approaches, and it’s capable of spotting unknown threats. However, such systems remain rule-informed rather than data-driven, and they don’t learn from previous experience.
- Anomaly detection solutions establish a baseline of “normal” system behavior based on usual network traffic and other activity. When behavior deviates from this baseline, these systems trigger alerts. This approach can detect previously unknown threats without relying on predefined rules, but it’s prone to generating false positives.
So, how is AI cyber threat detection different? In short, it’s significantly more adaptable and independent. Deep Learning models and neural networks can recognize complex and evolving threat patterns, detecting risks faster and with greater accuracy. Well-trained AI models also require minimal human input to operate, reducing the need for constant monitoring and manual updates. While they still need oversight and maintenance, they offer a more autonomous and scalable way to protect your business.
Key use cases for AI threat detection
Threat detection AI delivers security value across multiple domains. Its versatility is a strong advantage, but it also requires you to understand precisely what you’re trying to accomplish before integrating AI. Let’s review the most common and effective applications of this technology across different layers of security architecture.
Network security
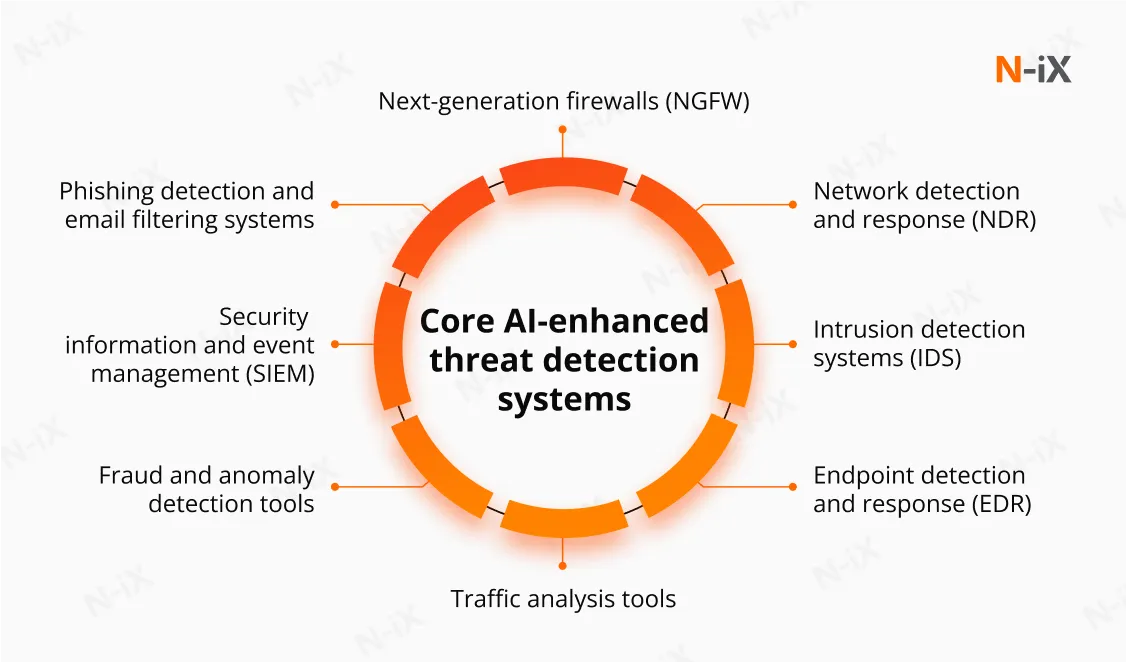
AI enhances network security by enabling real-time traffic analysis, pattern recognition, and faster threat identification. The following tools help put these capabilities into practice:
- AI-powered next-generation firewalls (NGFW) continuously analyze traffic patterns to rapidly identify potential cyberattacks. These systems establish baseline network behavior and flag deviations that could indicate security breaches.
- Network detection and response (NDR) solutions use AI to identify lateral movement, command-and-control activity, and other signs of intrusion that may evade traditional perimeter defenses.
- AI-based intrusion detection systems (IDS) analyze large volumes of network traffic to detect suspicious activity, even when it doesn’t match known attack signatures. These systems improve over time and reduce false positives, compared to traditional IDS.
- Tools for traffic analysis can use AI to spot threats without decrypting data.
Endpoint and system protection
Modern endpoint security uses AI-powered threat detection to safeguard individual devices within networks. AI-driven endpoint protection analyzes file behavior and system changes to identify even previously unknown threats.
AI also powers advanced endpoint detection and response (EDR) systems that monitor activities on endpoints in real time. These tools detect suspicious behavior, automate incident response, and provide forensic data to support investigations. AI-based malware detection systems further enhance protection. They identify malicious code by its behavior and structure, not just known signatures, making it more effective against zero-day attacks.
Learn more about choosing between EDR, MDR, and XDR
Threat monitoring and management
AI improves general threat monitoring by helping security teams detect, prioritize, and respond to risks more effectively. The following AI-driven solutions illustrate how these capabilities are applied in practice:
- AI-powered security information and event management (SIEM) solutions process vast volumes of logs and security events in real time. They correlate activity across multiple systems to pinpoint genuine threats faster and reduce alert fatigue.
- AI-driven vulnerability monitoring can identify unpatched software or outdated components by scanning system configurations and flagging risks. This kind of automation may have helped prevent the Equifax breach, as the patch for the exploited vulnerability existed but wasn’t applied in time.
- Phishing detection and email filtering systems use AI to analyze message content, metadata, and user behavior to identify suspicious emails. These tools adapt to evolving tactics and reduce the risk of users interacting with harmful links or attachments.
- Fraud and anomaly detection tools monitor user behavior and access patterns to flag unusual actions signaling account compromise or insider threats.
Identity and access protection
AI transforms identity and access management by continuously monitoring authentication patterns and user behaviors. These systems establish baselines for “normal” behavior for each identity and quickly flag deviations that may indicate compromised credentials.
Although it looks similar to broader anomaly detection tools, AI makes context-aware access decisions. For example, it can identify if the location, device, and behavior during a login attempt match that particular user’s regular profile. This enables AI systems to determine when a seemingly valid login is actually an attacker using stolen credentials based on subtle behavioral cues.
Implementing AI threat detection in your organization
AI can greatly enhance your security posture, but it requires a clear plan, high-quality data, and the right technical foundation. Let’s walk through the key steps to successfully integrate Artificial Intelligence into your organization’s security ecosystem.
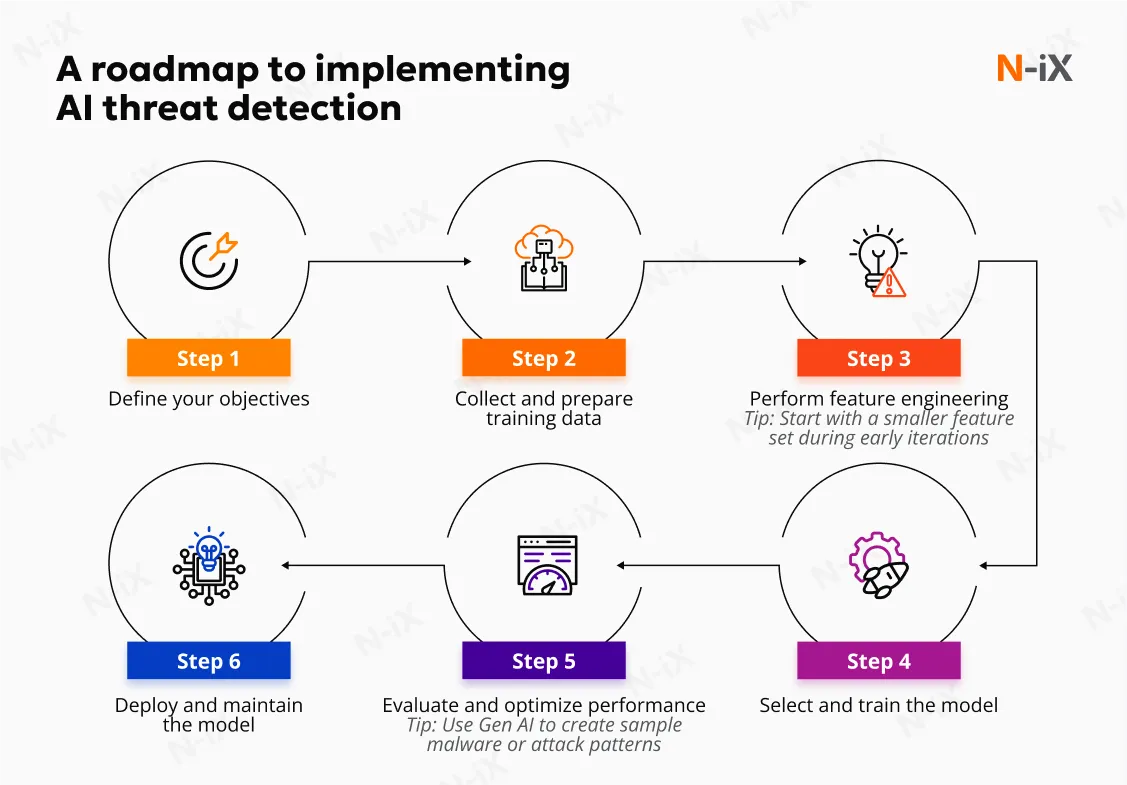
1. Define your goals
Start by identifying the specific threats your organization faces. The implementation process will largely depend on what you’re planning to prioritize, whether it’s protection against network intrusions, malware, or credential theft.
N-iX security specialists also recommend “beginning with the end in mind.” Define metrics that will measure success, such as detection rates or response times. These benchmarks will help you evaluate the performance of your AI tools over time and adjust your strategy based on the outcomes.
2. Collect and prepare data
AI-driven threat detection thrives on high-quality data. Prepare to train your model by collecting relevant logs from network traffic, system events, and user activity records. Then, ensure that the data is cleaned, normalized, and consistently formatted. Our AI engineers stress that raw data alone isn’t enough. Proper preprocessing and labeling at this stage are crucial to enable accurate learning and reliable detection later on.
3. Perform feature engineering
Effective Machine Learning in cybersecurity requires you to identify meaningful indicators of malicious activity. This process is called feature engineering. After preparing your data, pinpoint variables that represent suspicious or noteworthy behavior, such as unusual login times, data transfer spikes, or access to sensitive files. Focus on selecting features that are relevant to your specific threat scenarios.
A tip from N-iX data scientists: Start with a smaller, well-defined feature set to improve model clarity during early iterations.
4. Select and train the model
Choose a model type that aligns with your specific security objectives. Several options include:
- Supervised learning for detecting known threats;
- Unsupervised learning for identifying anomalies without predefined labels;
- Deep Learning for recognizing complex patterns across large datasets.
Once your AI threat detection model is selected, train it on your prepared data to distinguish between normal and suspicious behavior.
5. Evaluate and optimize the model
When the model is trained, thoroughly test it to assess accuracy, response times, and its ability to identify both known and novel threats. Validation helps fine-tune detection parameters and identify areas for improvement before relying on this system for protection.
A tip from N-iX experts: Generative AI can be used here to create sample malware or attack patterns, helping you evaluate how well the model detects unfamiliar threats.
Discover more use cases of GenAI in cybersecurity
6. Deploy and maintain
At this stage, it’s time to integrate your trained and tested AI system with your existing security infrastructure. This often requires connecting with SIEM platforms, EDR systems, and other monitoring tools to ensure seamless response coordination.
Additionally, while AI-driven systems typically require less hands-on tuning than rule-based tools, deployment is not the final step. Ongoing maintenance is paramount to ensure the solution stays effective as threats evolve and environments change. Make sure to periodically retrain the model with fresh data, update it as business priorities or compliance requirements change, and monitor for performance drift.
Practical considerations before adopting AI threat detection
Integrating AI into any area of business should balance innovation with practical readiness. Before moving forward, it’s important to evaluate how AI fits into your existing environment, understand potential AI security risks, and determine what it takes to support automated threat detection at scale. Here are several core considerations to plan ahead for:
- Adopting a hybrid approach: AI adds powerful capabilities, but it shouldn’t replace human expertise or existing controls. A hybrid approach where AI works alongside analysts and traditional tools offers better reliability and context-aware decision-making.
- Choosing a qualified tech consultant: Integrating AI into your security stack involves data preparation, architectural changes, and ongoing maintenance. Consider partnering with someone like N-iX to get access to both cybersecurity and AI development expertise. This helps avoid common implementation pitfalls and ensures the solution aligns with both real-world threat scenarios and your strategic requirements.
- Staff training and operational readiness: Introducing AI changes how security teams operate. Ensure your staff understands how the new system works, how to interpret alerts, and when to intervene.
- Cost and scalability: AI implementations vary in complexity. Evaluate both the upfront investment and long-term costs of scaling your solution as your organization grows or faces new threats. Consider implementing cost optimization strategies to establish tighter control over your expenses from the start.
- Data privacy and compliance: AI models require access to sensitive data for training and operation, which can raise privacy concerns. Build your system with security regulations in mind and ensure data handling aligns with industry standards and compliance requirements.
Conclusion
AI threat detection stands at the forefront of modern cybersecurity strategies for good reason. Organizations face increasingly sophisticated attacks while traditional detection methods struggle to keep pace. We’ve explored how AI transforms threat detection capabilities across networks, endpoints, identity systems, and monitoring solutions throughout this guide.
However, successful implementation requires relevant expertise. Choosing the right technology consulting partner can help you navigate the complexities of AI integration and ensure the solution aligns with your strategic objectives.
Why should you implement AI threat detection with N-iX?
N-iX is a global cybersecurity and AI consulting provider, trusted by more than 160 active clients. We combine deep technical knowledge with practical experience and industry best practices to deliver reliable and adaptable AI-driven threat detection solutions.
By partnering with N-iX, you receive:
- A team of more than 2,400 tech professionals, including over 200 specialized data, AI, and ML engineers working closely with cybersecurity experts and cloud architects;
- Proven track record of over 100 projects strengthening clients’ security posture across diverse industries, including banking, telecom, and IT services;
- Adherence to rigorous security standards, including CyberGRX, ISO 27001, ISO/IEC 27701:2019, PCI DSS, and FSQS.
Whether you’re just starting your AI security journey or looking to enhance existing capabilities, we are ready to help you innovate confidently. Let’s discuss a strategic path forward and minimize your security risks together.
Have a question?
Speak to an expert




